Zero Trust Security: Why “Never Trust, Always Verify” is the New Standard

The digital world is breaking boundaries, enabling access, and opening up a world of opportunities – but only if it’s secure.
For decades, IT departments relied on encrypted networks and complex architectures. But today, that’s simply not enough. Modern threats require a modern solution: Zero Trust.
At microtom, we’re moving beyond the traditional security perimeter and embracing Microsoft’s Zero Trust model.
What is Zero Trust?
Never trust. Always verify.
This principle means that no user or device is automatically trusted, no matter where they’re connecting from. Every request must be verified before access is granted.
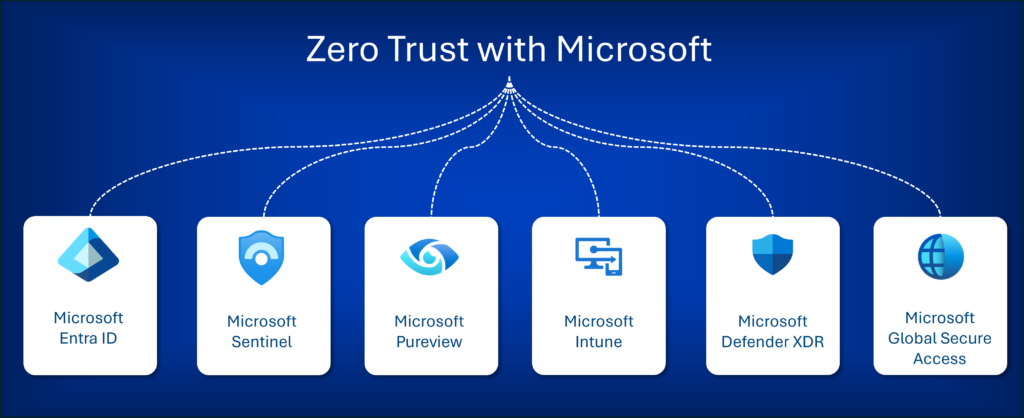
How we implement Zero Trust with Microsoft
We use Microsofts cloud-native tools to create a secure, compliant, and flexible IT environment:
Microsoft Entra ID
Multi-Factor Authentication (MFA) and dynamic Conditional Access rules ensure that access is only granted when all conditions are securely met.
Microsoft Sentinel
Real-time monitoring and automated threat detection enable early response to suspicious activity.
Microsoft Pureview Information Protection
Data remains protected both in the cloud and on-premises through encryption and access control policies.
Microsoft Intune
Ensures only secure and compliant devices can connect to your company’s resources.
Microsoft Defender XDR
Provides organization-wide visibility, threat detection, and rapid incident response in a unified interface.
Microsoft Global Secure Access
Replaces traditional VPNs with granular, role-based access. Internal systems are only available to the users or teams who need them—nothing more.
Why It Matters
With Zero Trust, you gain a security model that is:
- Flexible for remote and hybrid work
- Scalable across all departments
- Aligned with modern compliance requirements
- Focused on proactive protection instead of reactive fixes
Let’s Talk Security
Want to know how Zero Trust can protect your infrastructure and data?
Let’s get in touch — we’re here to help.




